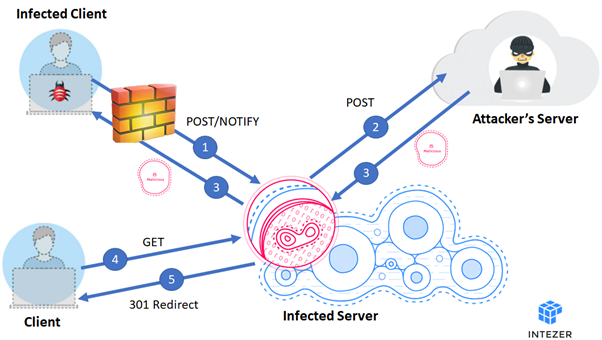
According to ESET researchers reporting, cybercriminals, who created Stantinko mining botnet, developed also several obfuscation methods in order not to be found.
Vladislav Hrčka, an associate of ESET internet security company, who is responsible for malware analysis, revealed a recent result of the research and told about activities that can be taken against the botnet providers on his webpage.
«People who created Stantinko botnet are improving their skills and introducing new models which include original and unpredictable methods, » he noted.
This botnet appeared in 2012 and is being spread with the help of malware, which is embedded in piracy files. The main targets of Stantinko are users from following countries: Russian Federation, Kazakhstan and Ukraine. At first, it was doing users activity fraud, advertising integration, SM fraud, and passwords’ theft. Nevertheless, in the middle of 2018 the owners of the botnet added to its profile a new hidden mining module Monero for cryptocurrency.
Monero includes such elements that are capable to find antivirus program and stop all other cryptocurrency mining processes. The module exhausts almost all assets of the chosen machine, and at the same time stops its intervention in order not to be found when a PC owner clicks on Task Manager to figure out why the device works so slow.
Stantinko platform doesn’t interact with pool of the miners and prefers to use proxy servers. Digital security company ESET discovered the previous reporting about cryptocurrency fraud module in the middle of autumn last year, however since that time the botnet providers found other methods to avoid being found:
- Strings entanglement – this is a tool when the most important strings are created and can be visible in back-office only when users need to see them.
- Non-working strings and assets – a method when assets and strings are added without impacting functionality.
- Entanglement of the managing commands flow– conversion of the managing commands into a tough-readable form to make the order of basic elements unpredictable.
- Non-existing code – a command that never functions, and its unique objective is to adopt files so they could look more legitimate.
- Non-active code – a technique of code introducing that is done but has no sense and does nothing. With this method it is easy to trick behavioral founding.
«The most notable details of Stantinko is the manner it functions and how it thwarts analysis and finding. Because it uses source-level entanglements with a seed of random and that Stantinko’s creators adjust the tool for every victim, each sample is non-repeating,» mentioned Hrčka in first reporting. As we informed previously, in September a new miner virus Skidmap for Linux operating system was discovered. This virus is covering up its activity.